1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
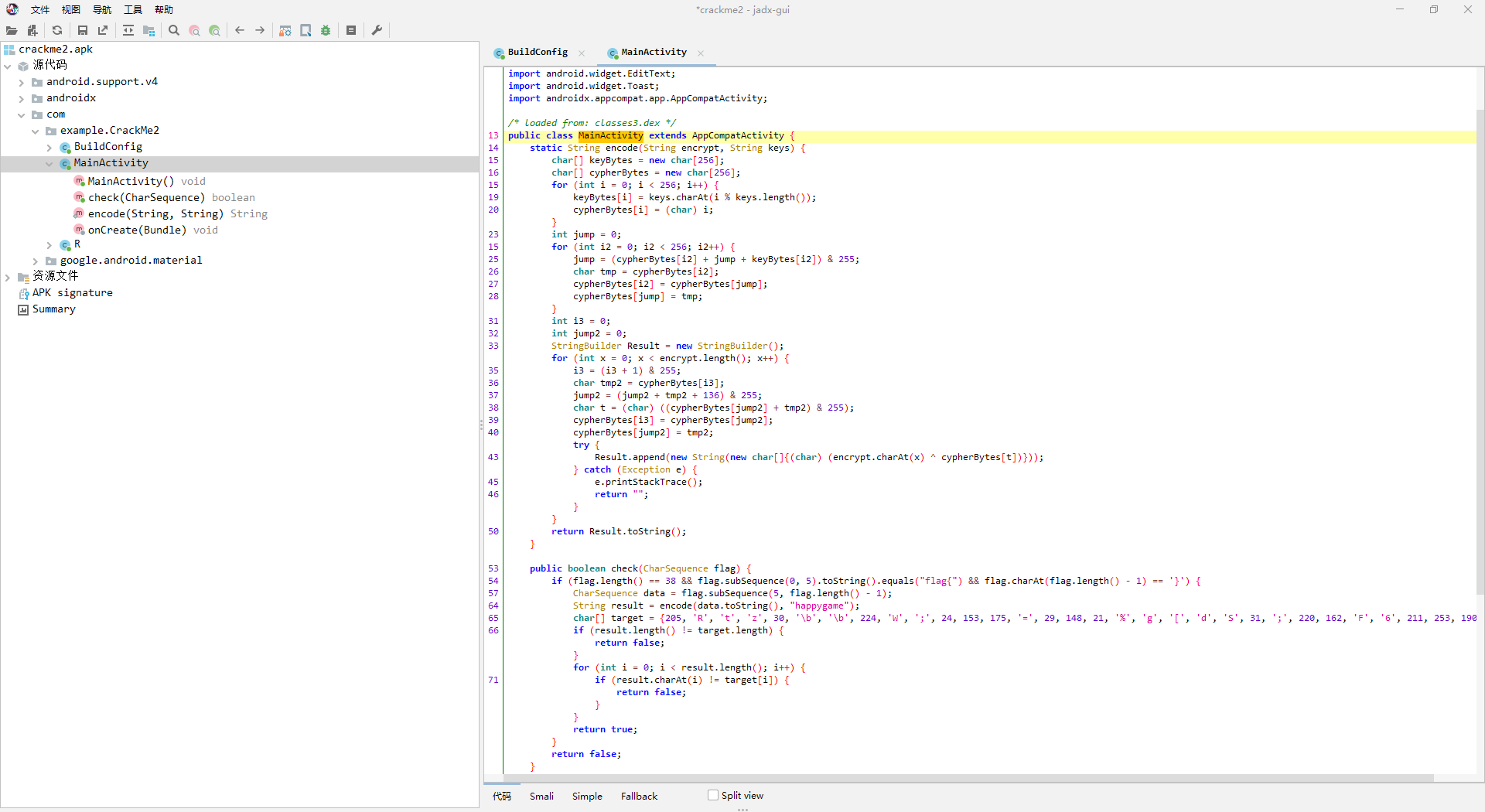
| public class wp{
public static String encode(char[] encrypt, String keys) {
char[] keyBytes = new char[256];
char[] cypherBytes = new char[256];
for (int i = 0; i < 256; i++)
{
keyBytes[i] = keys.charAt(i % keys.length());
cypherBytes[i] = (char) i;
}
int jump = 0;
for (int i2 = 0; i2 < 256; i2++) {
jump = (cypherBytes[i2] + jump + keyBytes[i2]) & 255;
char tmp = cypherBytes[i2];
cypherBytes[i2] = cypherBytes[jump];
cypherBytes[jump] = tmp;
}
int i3 = 0;
int jump2 = 0;
StringBuilder Result = new StringBuilder();
for (int x = 0; x < encrypt.length; x++) {
i3 = (i3 + 1) & 255;
char tmp2 = cypherBytes[i3];
jump2 = (jump2 + tmp2 + 136) & 255;
char t = (char) ((cypherBytes[jump2] + tmp2) & 255);
cypherBytes[i3] = cypherBytes[jump2];
cypherBytes[jump2] = tmp2;
try {
Result.append(new String(new char[]{(char) (encrypt[x] ^ cypherBytes[t])}));
} catch (Exception e) {
e.printStackTrace();
return "";
}
}
return Result.toString();
}
public static void main(String[]args){
char[] target = {205, 'R', 't', 'z', 30, '\b', '\b', 224, 'W', ';', 24, 153, 175, '=', 29, 148, 21, '%', 'g', '[', 'd', 'S', 31, ';', 220, 162, 'F', '6', 211, 253, 190, '3'};
String result =encode(target,"happygame");
System.out.println("flag{"+result+"}");
}
}
|